Reasons for Implementing Multi-Tenant Isolation Technology
This technology is particularly significant within the AIGC full-stack architecture. In the Software as a Service (SaaS) layer, multi-tenant isolation ensures that each tenant can access independent and customized AI application services. This guarantees that any modifications or upgrades to a specific tenant's service do not disrupt the services of other tenants. Such independence greatly enhances user satisfaction and the overall quality of service. Moreover, given that the SaaS layer frequently processes substantial amounts of user data, including sensitive information, multi-tenant isolation provides a robust privacy protection barrier at the data level, ensuring both security and compliance.
In the Platform as a Service (PaaS) layer, multi-tenant isolation technology plays an equally important role. It facilitates fine-grained resource partitioning and dynamic allocation, enabling different tenants to flexibly acquire the resources they require based on their business needs. This approach not only optimizes resource utilization but also accelerates business response times. Additionally, this technology ensures the isolation of the AI software stack among tenants, thus preventing interference related to software versions, configurations, and dependencies, which in turn maintains the stability and consistency of the software architecture.
The implications of multi-tenant isolation technology at the Infrastructure as a Service (IaaS) layer are also noteworthy. It enables the efficient sharing of hardware resources among multiple tenants, thereby minimizing resource waste and idleness. Although multi-tenant technology has achieved logical tenant isolation, it remains imperative for the IaaS layer to implement physical isolation measures. Such measures are necessary to guarantee the security and reliability of data centre services, preventing potential chain reactions that could adversely affect multiple tenants in the event of physical attacks or failures. Through these initiatives, multi-tenant isolation technology within the IaaS layer provides strong assurance of stability and security for the AIGC full-stack architecture.
Challenges Faced by Multi-Tenant Isolation Technology
2. Performance Interference: The shared nature of resources in a multi-tenant environment can result in one tenant's resource usage adversely affecting the performance of others. This phenomenon, often referred to as the "neighbour effect," occurs when the high resource demands of one tenant disrupt the operational efficiency of adjacent tenants.
3. Compliance Issues: Certain tenants may be subjected to specific regulatory or compliance standards that impose particular requirements for data isolation and access control within a multi-tenant framework. Meeting these compliance obligations may necessitate additional investment and the development of complex solutions.
4. Technical Complexity: The successful implementation of multi-tenant isolation often demands sophisticated technical solutions, including virtualization, containerization, and network isolation. These technologies can increase the complexity associated with deployment and management, often requiring the involvement of specialized personnel for effective support.
In summary, while multi-tenant isolation technology offers significant advantages in public cloud environments, it concurrently faces notable challenges. To optimize these benefits and address potential drawbacks, cloud service providers must adopt appropriate security measures, performance optimization strategies, compliance solutions, and technical support mechanisms.
Regarding the implementation of multi-tenant isolation technology in AIGC networks, several methodologies may be employed:
● Access Control and Security Policies: The establishment of stringent access controls and security policies, such as Access Control Lists (ACLs), ensures that only authorized tenants may access specific data and resources.
It is pertinent to note that VXLAN technology introduces two additional considerations for AIGC networks. The first issue is performance overhead; VXLAN necessitates extra processing for packet encapsulation and DE capsulation, resulting in a header byte overhead, particularly under conditions of high network load. Secondly, cross-network support presents a challenge; VXLAN typically requires approval and compatibility from underlying network devices, including switches and routers. Implementing VXLAN across disparate network domains or cloud providers may encounter compatibility and integration obstacles.
The use of ACLs for multi-tenant isolation also entails its own set of challenges. The first issue pertains to maintenance complexity; managing a large number of access control entries required for multi-tenant isolation can complicate configuration and maintenance efforts. Secondly, the static nature of ACL rules can inhibit adaptability; as these rules are usually preconfigured, they may not easily respond to the dynamically changing network environment. In scenarios where access policies necessitate frequent modifications, ACLs may prove insufficiently flexible.
Ruijie's "VRF Penetration" Solution
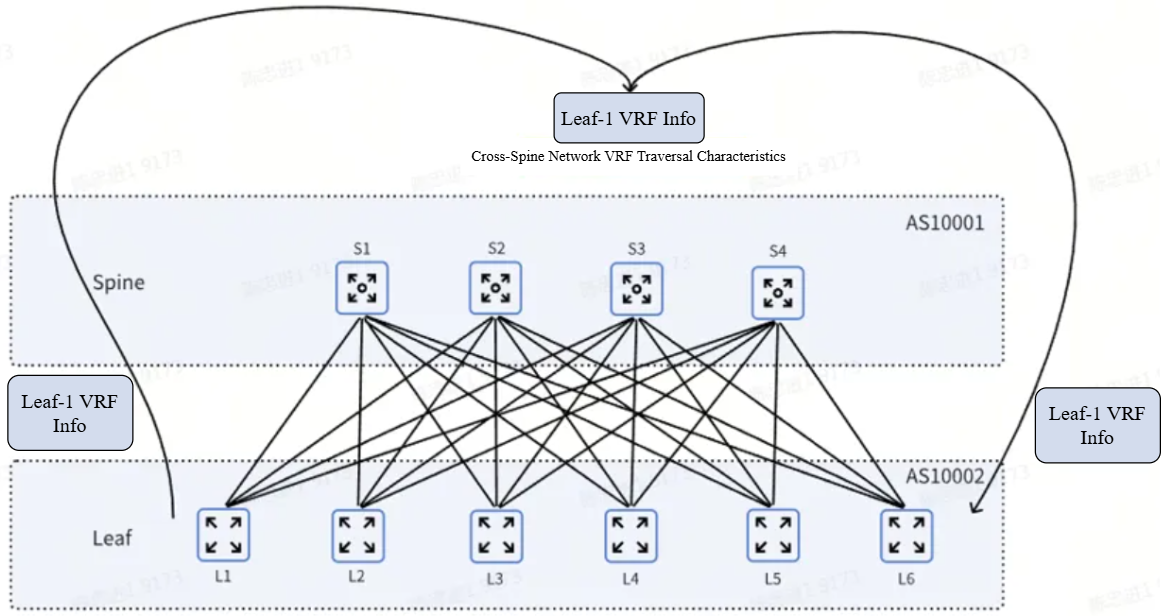
VRF (Virtual Routing and Forwarding) is a sophisticated technology designed to establish multiple virtual routing tables within a singular physical router or switch. Each of these virtual routing tables is identified as a VRF instance, and they operate independently, enabling the coexistence of numerous VRF instances on a single device. This technology facilitates the virtualization of routing tables, thereby allowing the creation of distinct virtual routing environments. Each VRF instance maintains its independent routing table, containing routing information pertinent to the specific network it serves, while information from other VRF instances remains inaccessible to any particular instance. Consequently, the routing information among different VRF instances is entirely segregated.
1. Resource Isolation: Each VRF instance possesses an independent routing table and forwarding logic, which guarantees the isolation of network traffic across diverse tenants. This feature ensures that the network resources of each tenant remain unaffected by those of others, thereby enhancing both security and stability within the network.
2. Flexibility: The implementation of VRF technology allows for the establishment of multiple VRF instances on a single physical device, with the capacity to allocate varying network resources according to specific requirements, such as interfaces, IP addresses, and routing information. This inherent flexibility enables dynamic adjustments and effective management of resource allocation among tenants based on prevailing conditions.
3. Simplified Deployment: Effective traffic isolation can be accomplished by deploying VRF exclusively at the Leaf node, thereby eliminating the necessity for intricate configurations on the Spine devices.
The implementation of multi-tenant isolation technology within the AIGC network is paramount for ensuring data security and maintaining stable performance. By leveraging virtualization technology, containerization, strict access controls, and robust security policies, mutual independence among tenants and the confidentiality of data can be achieved, thereby delivering secure and efficient AIGC services to enterprises. With the ongoing advancements in technology, it is anticipated that multi-tenant isolation will play an increasingly pivotal role in the AIGC network, generating significant value for enterprises.
Ruijie Networks, recognized as a full-stack service leader in the GenAI era, is committed to delivering comprehensive products and solutions encompassing IaaS to PaaS. Our offerings include the optimization and scheduling of high-performance networks and GPU computing capabilities, aimed at assisting clients in achieving significant improvements in production efficiency and operational cost optimization through innovative technological solutions. We are confident that our dedicated efforts will contribute to the creation of a more intelligent, efficient, and reliable future for our clients. Together, let us strive for excellence and explore every opportunity in the GenAI era.

Related Blogs:
Exploration of Data Center Automated Operation and Maintenance Technology: Zero Configuration of Switches
Technology Feast | How to De-Stack Data Center Network Architecture
Technology Feast | A Brief Discussion on 100G Optical Modules in Data Centers
Research on the Application of Equal Cost Multi-Path (ECMP) Technology in Data Center Networks
Technology Feast | How to build a lossless network for RDMA
Technology Feast | Distributed VXLAN Implementation Solution Based on EVPN
Exploration of Data Center Automated Operation and Maintenance Technology: NETCONF
Technical Feast | A Brief Analysis of MMU Waterline Settings in RDMA Network
Technology Feast | Internet Data Center Network 25G Network Architecture Design
Technology Feast | The "Giant Sword" of Data Center Network Operation and Maintenance
Technology Feast: Routing Protocol Selection for Large Data Centre Networks
Technology Feast | BGP Routing Protocol Planning for Large Data Centres
Technology Feast | Talk about the next generation 25G/100G data centre network
Technology Feast | Ruijie Data Center Switch ACL Service TCAM Resource Evaluation Guide
Silicon Photonics Illuminates the Path to Sustainable Development for Data Centre Networks
How CXL Technology Solves Memory Problems in Data Centres (Part 1)
CXL 3.0: Solving New Memory Problems in Data Centres (Part 2)
Ruijie RALB Technology: Revolutionizing Data Center Network Congestion with Advanced Load Balancing
Featured blogs
- CXL 3.0: Solving New Memory Problems in Data Centres (Part 2)
- Ruijie RALB Technology: Revolutionizing Data Center Network Congestion with Advanced Load Balancing
- Multi-Tenant Isolation Technology in AIGC Networks—Data Security and Performance Stability
- Multi-dimensional Comparison and Analysis of AIGC Network Card Dual Uplink Technical Architecture
- A Brief Discussion on the Technical Advantages of the LPO Module in the AIGC Computing Power Network











